ページの先頭です。
ここから本文です。
ACL Setting Procedure (ZEQUO Series)
Introduction
This setting example explains the procedure of ACL setting for ZEQUO series switches.
Applicable models
| Applicable models | |
|---|---|
| Product name | Product number |
| ZEQUO 6400 | PN36240E |
| ZEQUO 2200 | PN26241 |
| ZEQUO 2210 | PN26161 |
Overview
Set VLAN on ZEQUO series switch.
Configure ACL to control communication within the VLANs.
Configuration Example
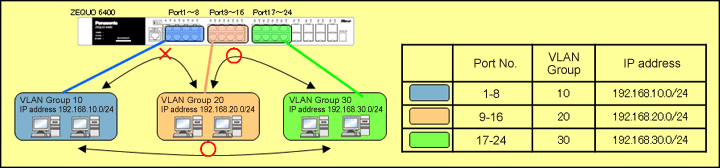
Overall setting flow
- 1. Set Ports 1-8 to VLAN Group10 (VID=10 VLAN NAME=Group10), IP:192.168.10.254/24.
- 2. Set Ports 9-16 to VLAN Group20 (VID=20 VLAN NAME=Group20), IP:192.168.20.254/24.
- 3. Set Ports 17-24 to VLAN Group30 (VID=30 VLAN NAME=Group30), IP:192.168.30.254/24.
- 4. Set ACL to control and disable communication between VLAN Group10 and VLAN Group20.
Setting Procedure
Step 1.
Connect the PC and Ethernet Switch using a twisted pair cable and console cable, and display the setting screen on Hyper terminal.
(Refer to Setting Example "Ethernet Switch Connection Procedure to a Console Port" for the procedure to display the setting screen on the console port)
Step 2.
On the login screen, enter UserName and PassWord (both set as manager by default), and login to the setting screen.(Refer to Figure 1)
Step 3.
Set VLAN for ZEQUO 6400.
After Z6400:admin#, enter command as shown in the following.
Z6400:admin#config vlan default delete 1-28
If the command is entered correctly, the following will be displayed.
Command: config vlan default delete 1-28
Success.
Then, set VLAN Group10, 20, and 30.
Z6400:admin#create vlan Group10 tag 10
Command:create vlan Group10 tag 10
Success.
Z6400:admin#config vlan Group10 add untagged 1-8
Command:config vlan Group10 add untagged 1-8
Success.
Z6400:admin#config port_vlan 1-8 pvid 10
Command:config port_vlan 1-8 pvid 10
Success.
Z6400:admin#create vlan Group20 tag 20
Command:create vlan Group20 tag 20
Success.
Z6400:admin#config vlan Group20 add untagged 9-16
Command:config vlan Group20 add untagged 9-16
Success.
Z6400:admin#config port_vlan 9-16 pvid 20
Command:config port_vlan 9-16 pvid 20
Success.
Z6400:admin#create vlan Group30 tag 30
Command:create vlan Group30 tag 30
Success.
Z6400:admin#config vlan Group30 add untagged 17-24
Command:config vlan VLAN30 add untagged 17-24
Success.
Z6400:admin#config port_vlan 17-24 pvid 30
Command:config port_vlan 17-24 pvid 30
Success.
Step 4.
Set the IP address for ZEQUO 6400.
IP interfaces of Group10, Group20, and Group30 are IP10 and IP20, and IP30, respectively.
Z6400:admin#config ipif System ipaddress 0.0.0.0/0 vlan default
Command:config ipis System ipaddress 0.0.0.0/0 vlan default
Success.
Z6400:admin#create ipif IP10 192.168.10.254/24 Group10 state enable
Command:create ipif IP10 192.168.10.254/24 Group10 state enable
Success.
Z6400:admin#create ipif IP20 192.168.20.254/24 Group20 state enable
Command:create ipif IP20 192.168.20.254/24 Group20 state enable
Success.
Z6400:admin#create ipif IP30 192.168.30.254/24 Group30 state enable
Command:create ipif IP30 192.168.30.254/24 Group30 state enable
Success.
Step 5.
Set ACL for ZEQUO 6400.
Set to disable communication between Group10 and VLAN Group20.
First, create access list profile with the subnet mask of the target IP addresses.
Z6400:admin#create access_profile profile_id 1 profile_name ACL_Rule_1 ip source_ip_mask 255.255.255.0 destination_ip_mask 255.255.255.0
Command:create access_profile profile_id 1 profile_name ACL_Rule_1 ip source_ip_mask 255.255.255.0 destination_ip_mask 255.255.255.0
Success.
Step 6.
Then, enter the target IP addresses on the profile created in Step 5 to set a control method.
Z6400:admin#config access_profile profile_id 1 add access_id 1 ip source_ip 192.168.10.0 mask 255.255.255.0 destination_ip 192.168.20.0 mask 255.255.255.0 port 1-8 deny
Command:config access_profile profile_id 1 add access_id 1 ip source_ip 192.168.10.0 mask 255.255.255.0 destination_ip 192.168.20.0 mask 255.255.255.0 port 1-8 deny
Success.
Step 7.
Create an entry of IP addresses in which the source and destination of the entry created in Step 6 are switched.(In order to control network communication from both ways.)
Z6400:admin#config access_profile profile_id 1 add access_id 2 ip source_ip 192.168.20.0 mask 255.255.255.0 destination_ip 192.168.10.0 mask 255.255.255.0 port 9-16 deny
Command:config access_profile profile_id 1 add access_id 2 ip source_ip 192.168.20.0 mask 255.255.255.0 destination_ip 192.168.10.0 mask 255.255.255.0 port 9-16 deny
Success.
Step 8.
When all the settings are complete, save the settings.
Z6400:admin#save
Command:save
Saving all configurations to NV-RAM.......... Done.
Step 9.
Check if the network communication between each VLAN is properly controlled.
ここからサブメニューです。